The following report is from Ars Technica:
The flaw, tracked as CVE-2022-0609, was exploited by two separate North Korean hacking groups. Both groups deployed the same exploit kit on websites that either belonged to legitimate organizations and were hacked or were set up for the express purpose of serving attack code on unsuspecting visitors. One group was dubbed Operation Dream Job, and it targeted more than 250 people working for 10 different companies. The other group, known as AppleJeus, targeted 85 users.
Dream Jobs And Cryptocurrency Riches
We suspect that these groups work for the same entity with a shared supply chain, hence the use of the same exploit kit, but each operate with a different mission set and deploy different techniques. It is possible that other North Korean government-backed attackers have access to the same exploit kit.
Adam Weidemann, a researcher on Google’s threat analysis group, wrote in a post.
Operation Dream Job has been active since at least June 2020, when researchers at security firm ClearSky observed the group targeting defense and governmental companies. Bad guys targeted specific employees in the organizations with fake offers of a “dream job” with companies such as Boeing, McDonnell Douglas, and BAE. The hackers devised an elaborate social-engineering campaign that used fictitious LinkedIn profiles, emails, WhatsApp messages, and phone calls. The goal of the campaign was both to steal money and collect intelligence.
AppleJeus, meanwhile, dates back to at least 2018. That’s when researchers from security firm Kaspersky saw North Korean hackers targeting a cryptocurrency exchange using malware that posed as a cryptocurrency trading application.
The AppleJeus operation was notable for its use of a malicious app that was written for macOS, which company researchers said was probably the first time an APT—short for government-backed “advanced persistent threat group”—used malware to target that platform. Also noteworthy was the group’s use of malware that ran solely in memory without writing a file to the hard drive, an advanced feature that makes detection much harder.
One of the two groups (Weidemann didn’t say which one) also used some of the same control servers to infect security researchers last year. The campaign used fictitious Twitter personas to develop relationships with the researchers. Once a level of trust was established, the hackers used either an Internet Explorer zero-day or a malicious Visual Studio project that purportedly contained source code for a proof-of-concept exploit.
In February, Google researchers learned of a critical vulnerability being exploited in Chrome. Company engineers fixed the vulnerability and gave it the designation CVE-2022-0609. On Thursday, the company provided more details about the vulnerability and how the two North Korean hackers exploited it.
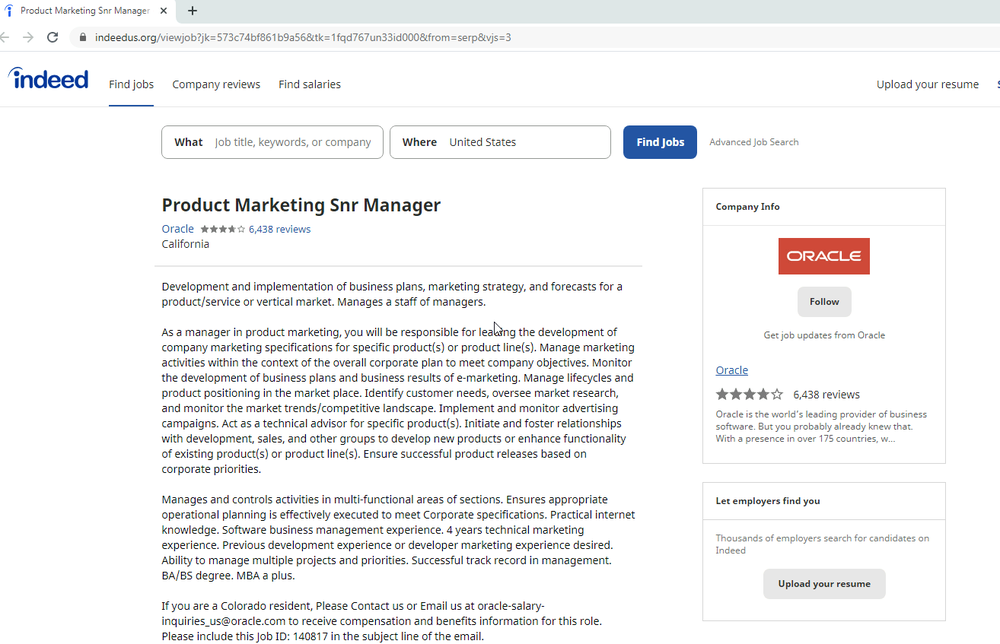
Operation Dream Job sent targets emails that purported to come from job recruiters working for Disney, Google, and Oracle. Links embedded into the email spoofed legitimate job hunting sites such as Indeed and ZipRecruiter. The sites contained an iframe that triggered the exploit.
Here’s an example of one of the pages used:
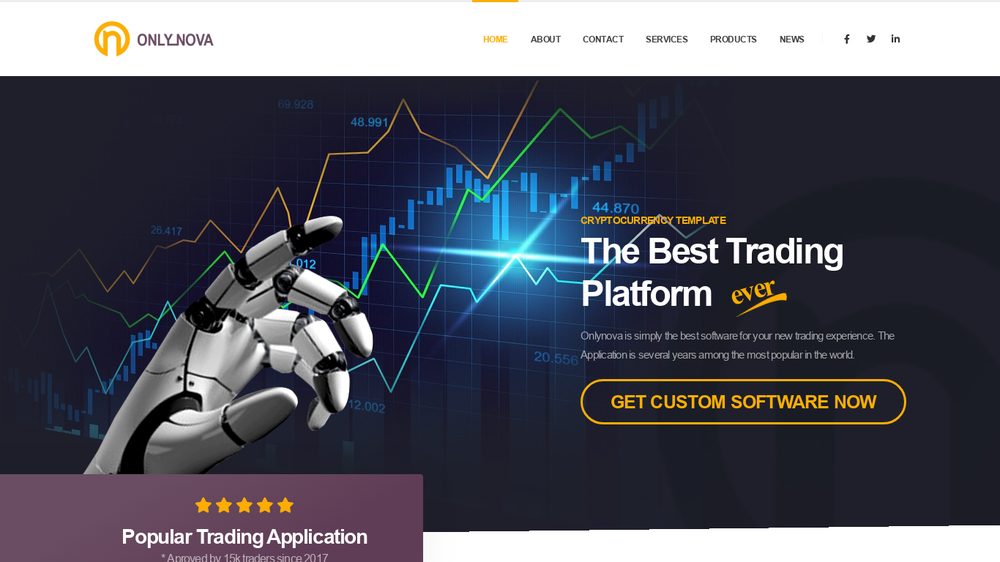
Members of Operation AppleJeus compromised the websites of at least two legitimate financial services companies and a variety of ad hoc sites pushing malicious cryptocurrency apps. Like the Dream Job sites, the sites used by AppleJeus also contained iframes that triggered the exploit.
Is There A Sandbox Escape In This Kit?
The exploit kit was written in a way to carefully conceal the attack by, among other things, disguising the exploit code and triggering remote code execution only in select cases. The kit also appears to have used a separate exploit to break out of the Chrome security sandbox. The Google researchers were unable to determine that escape code, leaving open the possibility that the vulnerability it exploited has yet to be patched.
Weidemann wrote:
The kit initially serves some heavily obfuscated javascript used to fingerprint the target system. This script collected all available client information such as the user-agent, resolution, etc. and then sent it back to the exploitation server. If a set of unknown requirements were met, the client would be served a Chrome RCE exploit and some additional javascript. If the RCE was successful, the javascript would request the next stage referenced within the script as “SBX”, a common acronym for Sandbox Escape. We unfortunately were unable to recover any of the stages that followed the initial RCE.
Careful to protect their exploits, the attackers deployed multiple safeguards to make it difficult for security teams to recover any of the stages. These safeguards included:
Only serving the iframe at specific times, presumably when they knew an intended target would be visiting the site.
In some email campaigns the targets received links with unique IDs. This was potentially used to enforce a one-time-click policy for each link and allow the exploit kit to only be served once.
The exploit kit would AES encrypt each stage, including the clients’ responses with a session-specific key.
Additional stages were not served if the previous stage failed.
Google researchers also found evidence the kit contained components that could exploit Safari for macOS and Firefox for all supported operating systems.
After Google patched the Chrome vulnerability on February 14, the hackers made multiple attempts to exploit the vulnerability. The finding “stresses the importance of applying security updates as they become available,” Weidmann said.
As of Thursday, only one antivirus engine detected the exploit kit, VirusTotal showed.
The analysis shows that North Korean hackers, often referred to under the umbrella name Lazarus, continue to step up their game by using many of the same advanced techniques their counterparts in other countries have been using for a decade or more. Anyone using a current version of Chrome is automatically protected against this campaign. It’s likely, however, that Lazarus will move on and find new vulnerabilities to exploit.
AUTHOR COMMENTARY
A prudent man foreseeth the evil, and hideth himself: but the simple pass on, and are punished.
Proverbs 22:3
If you’re like me, I don’t believe North Korea was involved in this, Lord only knows: you can’t trust anything the media tells us. If anything, this was to not only continually fuel the fears and the ‘Problem’ of the Hegelian Dialectic in play per a cyber attack, and to keep the animosity of North Korea in the media.
[7] Who goeth a warfare any time at his own charges? who planteth a vineyard, and eateth not of the fruit thereof? or who feedeth a flock, and eateth not of the milk of the flock? [8] Say I these things as a man? or saith not the law the same also? [9] For it is written in the law of Moses, Thou shalt not muzzle the mouth of the ox that treadeth out the corn. Doth God take care for oxen? [10] Or saith he it altogether for our sakes? For our sakes, no doubt, this is written: that he that ploweth should plow in hope; and that he that thresheth in hope should be partaker of his hope. (1 Corinthians 9:7-10).
The WinePress needs your support! If God has laid it on your heart to want to contribute, please prayerfully consider donating to this ministry. If you cannot gift a monetary donation, then please donate your fervent prayers to keep this ministry going! Thank you and may God bless you.